Network Cloaking for Zero Trust Security | CSOI® Cybersecurity Solutions
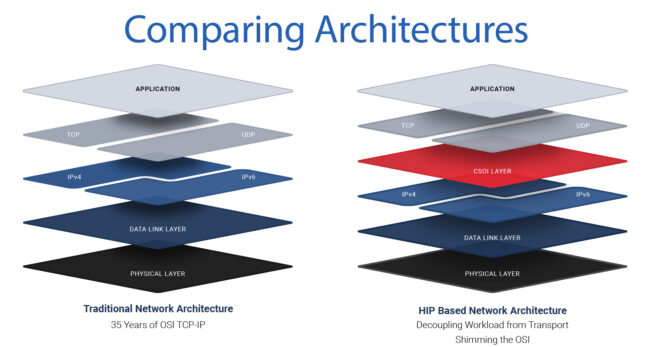
Making Critical Infrastructure Invisible to AttackersNetwork Cloaking with CSOI® network cloaking, network obfuscation, obscures devices, zero trust security, Layer 3.5 overlay, Host Identity Protocol, CSOI cybersecurity, OT network protection, operational…