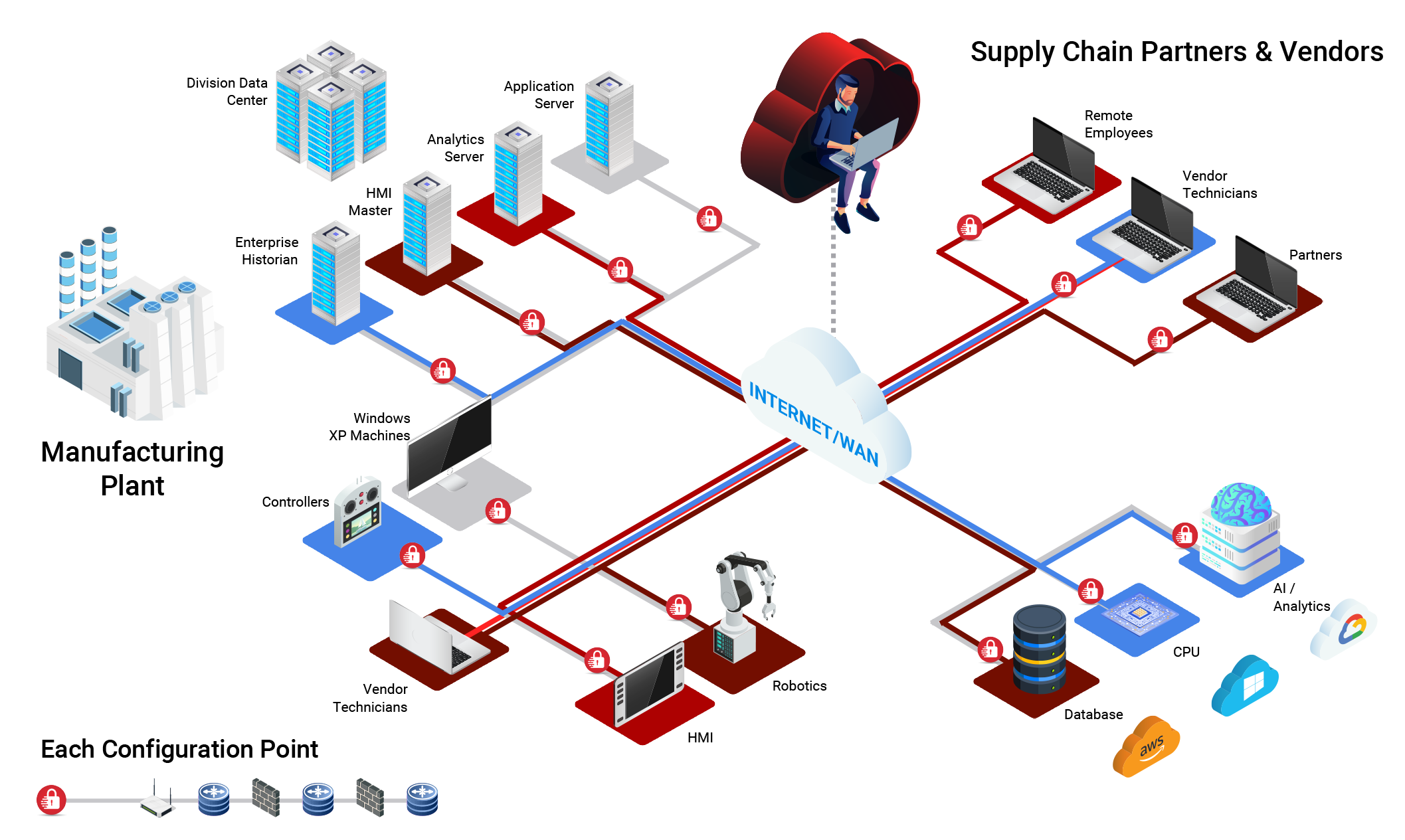
Effectively scaling, securing, and managing remote work can be nearly impossible with current open market solutions. It is even more difficult when your underlying network is breached or under attack. Legacy tactics of maintaining VPNs, ACLs, routing rules, and firewall policies are even harder to manage while supporting your remote workforce against your ever-changing hybrid infrastructure. Organizational networks with hardened perimeter security were designed with on-premises work in mind. In these situations, enabling support for coalition forces, remote support, or work activities with traditional remote access solutions, can inherently weaken an organizational network’s existing security posture.
Challenge: Scaling, Securing, and Managing Remote Access

Solution: Easily Enable Secure Remote Access at Scale
CSOI achieves zero-trust security and mobility for your entire workforce, wherever they are and for whatever they need to reach – globally. Leveraging RFC 5201, an essential cybersecurity framework; robust protection is enabled against network threats by implementing advanced security measures that safeguard critical data and ensure secure communication channels.
CSOI helps enable a Zero Trust Architecture (ZTA) security model providing secure, encrypted access from anywhere in the world. Create simple and easily segmented access policies to company resources for your entire workforce, while ensuring PCI, HIPAA, and NIST compliance. With CSOI, you can group users together in clusters, so they are invisible to others by default, and grant access to specific devices or resources as appropriate. With point-and-click simplicity, add or revoke access between devices on your network without the complexity of ACLs, routing rules, or firewall policies. Provision secure encrypted access between anything, anywhere — securely and easily.

Rapidly Deploy Secure Networks
Developed with agencies of all sizes and security classifications in mind, CSOI provides enterprise-wide cyber protection and security monitoring features without compromising network integrity or mission-critical operations. CSOI is founded on a Software-Defined Wide Area Network / Perimeter (SD-WAN) and Identity Defined Networking (IDN) architecture that seamlessly integrates networking and security into a unified platform that is topology, protocol, and hyper-visor agnostic. Our architecture proactively responds to workload placement, increases, decreases, and automatically moves resources to assist with logistical planning and resource allocations.

Reimagine Cybersecurity with CSOI
CSOI is a breakthrough in secure networking. It replaces traditional IP-based models with identity-driven networking to align with Zero Trust Architecture principles and eliminate cyber risk at the source.
- Cloak devices accessing sensitive data and intellectual property
- Support your organization’s security posture
- No need for rip-and-replace or wholesale network upgrades
- Easily add/revoke network access
- Maintain PCI, HIPAA, and NIST compliance
Solution Benefits
CSOI infrastructure is built to manage the most complex of network environments, including on-premises, public, private, and hybrid cloud environments. It is the only scalable, multi-use solution that creates a common secure networking architecture able to adapt to any connected resource – anytime and anywhere. Securing internal and remote access for employees becomes much more practical and cost-effective with CSOI. Networked elements can connect directly without the concern of opaque and complex legacy network constraints. With the CSOI ZTA architecture, you can reduce your attack surface by up to 90%, improving time to mitigation, revocation, and quarantine by up to 25%, while decreasing failover and disaster recovery to as little as one second.

Network Cloaking

Zero Trust Architecture

Micro Segmentation

Policy Defined Access
What We Offer

Cybersecurity Operations Infrastructure

CSOI VS. SD-WAN Solutions

CSOI vs VPN Solutions

Energy Systems Security
Surveillance Systems Security
Government Security

Executive Order 14028



